Belarusian Protesters Stung by a Malicious Geolocation-Leaking App
22 Sep 2020
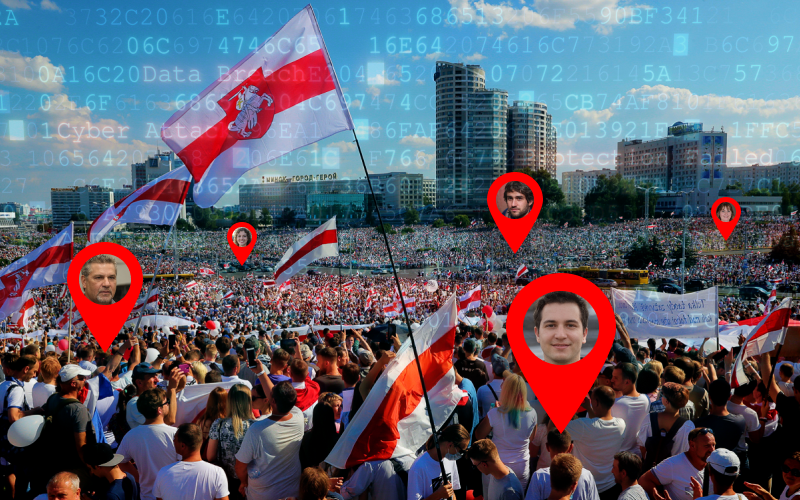
Anti-government protests and demonstrations in Belarus have taken center stage in the latest political news from Europe.
The people of Belarus are showing their discontent with the falsified elections, and autocratic leader Lukashenko has no intention of leaving his position. As a result, Belarusian police are getting involved in the operations to oppress the protests.
The police have raided Uber and Yandex offices in Minsk to get location data on those who use their voices.
The state is determined to get more information about protesting civilians, simultaneously censoring protest coverage by non-state-affiliated journalists. Besides mass detentions, Belarusian forces engaged in other types of crackdown, now focused around smartphones.
Knowing Where The Trap Is…
Today everyone knows just how much data our smartphones have on us, but seemingly everyone forgets about it all the same.
Devices store a lot of identifying information about its owners, and in the context of protests, smartphone owners would like to keep their data away from the government’s eye. This, in turn, leads to increased use of secure messengers that leverage encryption, and in some cases, make the user anonymous.
While using secure messengers is a good step in the right direction, just having such an application without following all the precautions and operational security can backfire. To give you an example, Hong Kong protesters found out a major security flaw in Telegram that unveiled the user's phone number.
It all happened almost exactly one year ago.
Now we can see that there are other approaches tested by the police to deanonymize people, but they do not exploit an app, but rather plant the app that exploits its users.
...The First Step In Evading It
So how are they doing it?
A bogus Android app was planted on PlayStore, mimicking as a trustworthy news source NEXTA to unveil the identities of those opposing the regime. NEXTA gained traction during the unrest and is regarded as a main news agency covering the protests.
The app named “NEXTA LIVE” was designed to track a user's geolocation, collect data from the owner’s device, and then upload it to a remote server. All while fronting as a hub for the latest news surrounding the demonstrations.
It’s not a complicated ploy, but it worked.
The malicious “NEXTA LIVE” app collected personal information of citizens involved in the protests and has been up for approximately three weeks, getting thousands of downloads. Upon discovering this trap-app, Nexta agency informed their Telegram subscribers about the dangers the application imposes, and encouraged them to report abuse and barrage the bogus app with negative reviews.
"Do not install under any circumstances. Warn your friends, maximum repost!," ‒ wrote Nexta staff in their Telegram channel.
That did the trick and got the app banned soon enough, but one has to wonder if thousands of people who downloaded this booby trap would be safe.
The state already has the necessary data and can act upon it, raiding meeting places and making a profile on those who are not happy with their current president, who has been in power for 26 years as of 2020.
It’s noteworthy that Belarus remains the only European country that has the capital punishment policy. Judging by the information provided in the “World Report 2020: Rights Trends in Belarus”, it seems like nothing is off the table for Alexander Lukashenko.
Impostors Among Us? Not Even In a Game
The future of deanonymized people is under threat however you look at it, whether they will or will not endure the draconian matters of punishment.
It takes very little to put yourself under the radar in Belarus, and action as futile as downloading an application may have drastic security implications, both virtual and physical. As people press on with their protests, they always have to keep in mind what the forces of be are doing to stop them. Aside from barricading the streets and restricting their movement, of course.
Police work comes in many forms, and this is just one example of how the government can use civilian devices for their goals. Evaluate your every step online when looking up the information that garners a lot of interest from the government.
Many people could have avoided that experience if the question about the legitimacy of the app was brought up earlier. The protest leaders should also understand that they bear responsibility in such a sensitive process, and must inform people about the latest “traps” online, which have to be closely monitored.
Lastly, if you can, avoid applications that offer you any kind of news. Lately, one application turned malicious and used a similar strategy to lure in users. Even though it wasn’t related to politics, the app used its user base to attack the popular security company.
Look up the news without downloading applications for it, never allow location tracking to apps that don’t need it, and always double-check the legitimacy of communication channels you’re using.
